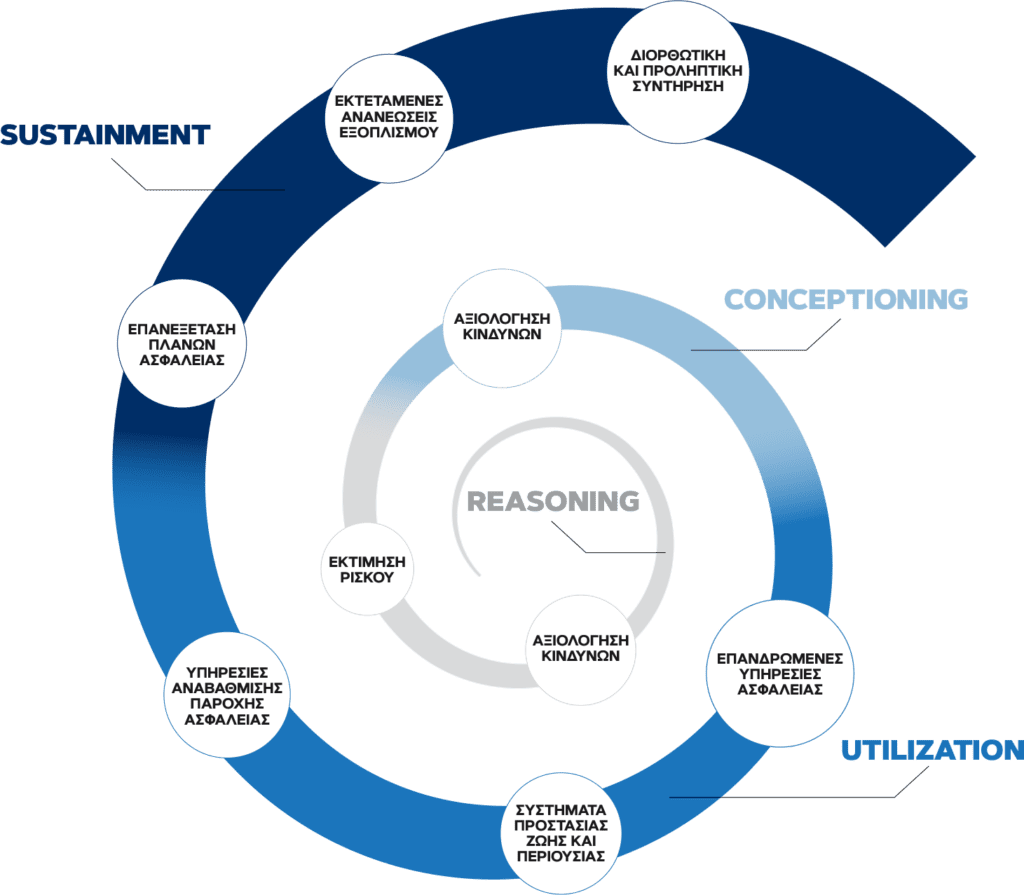
Reasoning
‘Why should we invest in security?’ The answer to this question comes after careful examination and recording of the threats that you might face. This answer then provides the starting point and the direction that the search for specific measures in order to manage the risks to life and the client’s property and operations will take.
• Risk Assessment
Together with you, ESA’s experienced risk assessment team will investigate and assess how specific threats can increase your security risk. We look for threats to the identity and operations of your organisation as they are revealed through analysis.
• Risk Evaluation
The quantifying of risk and therefore its evaluation is valuable information that will determine how much the organisation should spend to achieve a safe operational environment. ESA’s assessment team will work alongside you to determine the identity and extent of possible threats before and after specific measures are taken.